Secure Chain Ontology
Release: 2024-10-20
- This version:
- https://w3id.org/secure-chain/1.0.0
- Latest version:
- https://w3id.org/secure-chain
- Revision:
- 1.0.0
- Authors:
- Yifeng Di
- Hadi Askari
- Shushan Arakelyan
- Xiangyu Zhang
- Xiang Ren
- Muhao Chen
- Tianyi Zhang
- Extended Ontologies:
- Schema.org
- Download serialization:
- License:
- Visualization:
- Cite as:
- Yifeng Di, Hadi Askari, Shushan Arakelyan, Xiangyu Zhang, Xiang Ren, Muhao Chen, Tianyi Zhang. Secure Chain Ontology. Revision: 1.0.0. Retrieved from: https://w3id.org/secure-chain/1.0.0
Abstract
The Secure Chain Knowledge Graph is a comprehensive knowledge graph designed to model the relationships between software, hardware, vulnerabilities, and other entities to support secure and transparent management of software supply chains.Introduction back to ToC
In today's increasingly complex technological ecosystem, software has become an integral part of crucial infrastructures. Underlying modern software systems is the supply chain of open-source software components, such as Apache Spark, whose functionalities are reused and integrated into various systems underpinning modern society. While software supply chains empower the rapid development of software systems, they also increase the risks, since any bugs, vulnerabilities, and unauthorized changes in upstream components can propagate to downstream systems and cause severe consequences. This is evident through many software crises witnessed in recent years, such as the [Heartbleed bug](https://heartbleed.com/), the [Equifax data breach](https://www.securityweek.com/equifax-confirms-apache-struts-flaw-used-hack/#:~:text=U.S.%20credit%20reporting%20agency%20Equifax,used%20to%20breach%20its%20systems.), and the [NPM left-pad incident](https://qz.com/646467/how-one-programmer-broke-the-internet-by-deleting-a-tiny-piece-of-code) that almost broke the Internet. Therefore, the Secure Chain Ontology is designed to provide a unified knowledge graph ontology that can capture rich, up-to-date information about software components in heterogenous software ecosystems. By extending widely adopted ontologies such as [Schema.org](http://schema.org/) and incorporating principles from software description vocabularies, the Secure Chain Ontology facilitates interoperability with existing data sources and standards, making it a powerful tool for security professionals, developers, and researchers. The ontology supports key use cases such as risk analysis, secure software development lifecycle management, and compliance monitoring, by allowing users to trace dependencies between software and hardware components, identify which versions are affected by certain vulnerabilities, and ensure that all components in the chain are properly licensed. Additionally, the Secure Chain Ontology supports concepts such as vulnerability types and discovery, allowing for more detailed and actionable information when assessing the security posture of a system. As part of its design, the ontology aims to be flexible and extendable, enabling integration with domain-specific ontologies or other metadata vocabularies that may exist in different areas of the supply chain ecosystem.Namespace declarations
| dc | <http://purl.org/dc/elements/1.1/> |
| dcterms | <http://purl.org/dc/terms/> |
| owl | <http://www.w3.org/2002/07/owl#> |
| rdf | <http://www.w3.org/1999/02/22-rdf-syntax-ns#> |
| rdfs | <http://www.w3.org/2000/01/rdf-schema#> |
| sc | <https://w3id.org/secure-chain/> |
| schema | <http://schema.org/> |
| vann | <http://purl.org/vocab/vann/> |
| voaf | <http://purl.org/vocommons/voaf#> |
| widoco | <https://w3id.org/widoco/vocab#> |
| xml | <http://www.w3.org/XML/1998/namespace> |
| xsd | <http://www.w3.org/2001/XMLSchema#> |
Secure Chain Ontology: Overview back to ToC
This ontology has the following classes and properties.Classes
- Hardware
- Hardware Version
- License
- Organization
- Person
- Product
- Software
- Software Application
- Software Version
- Vulnerability
- Vulnerability Type
Object Properties
- affiliation
- contributor
- depends On
- discover
- has Hardware Version
- has Software Version
- license
- manufacturer
- operates On
- producer
- vulnerability Type
- vulnerable To
Data Properties
Secure Chain Ontology: Description back to ToC
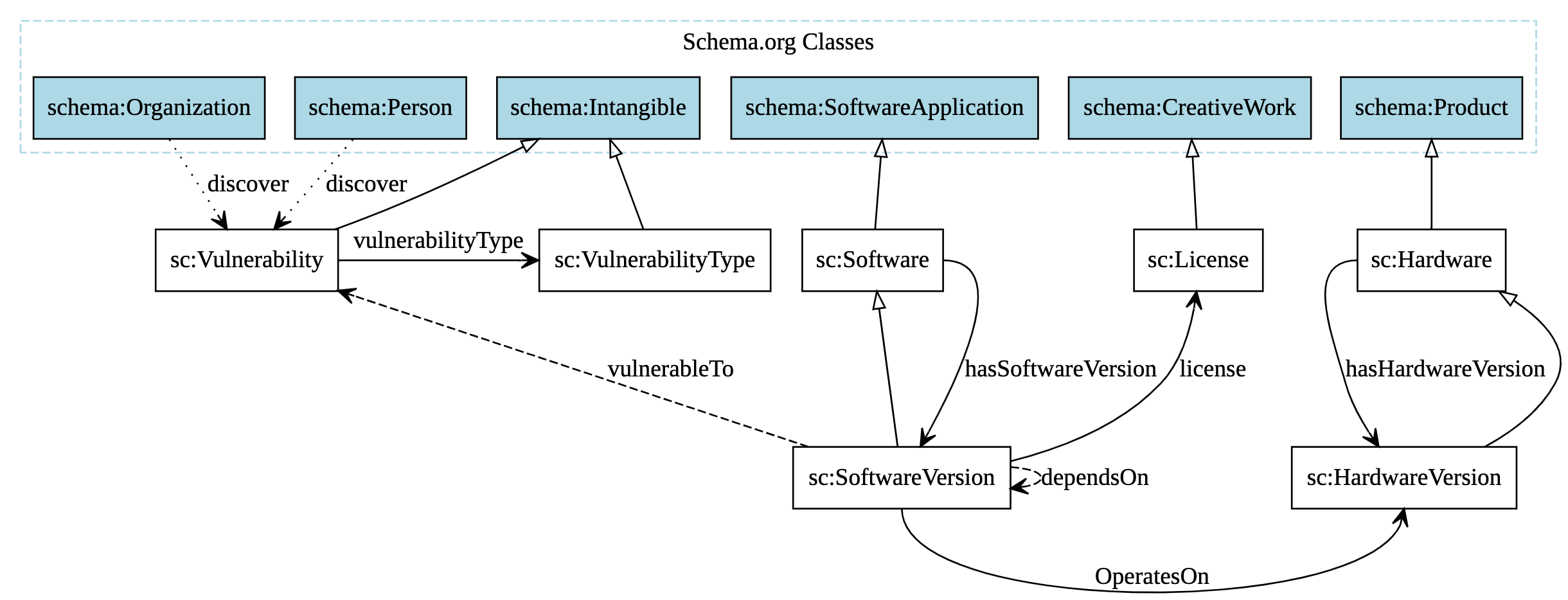
The Secure Chain Ontology builds on top of [Schema.org](http://schema.org/), as shown in the figure below, extending its vocabulary to seamlessly integrate with its metadata properties and enhance interoperability across various systems. We use sc:Software as a central concept in the Secure Chain Ontology to represent software within secure supply chains, with associated sc:SoftwareVersions capturing the evolution of software over time. These versions are critical for tracking vulnerabilities, compliance, and updates. The ontology models dependencies between software versions and other components, such as hardware, through properties like sc:dependsOn and sc:OperatesOn, which help assess potential risks and identify vulnerabilities. Additionally, sc:License links each software version to its legal aspects, ensuring compliance across the supply chain. The ontology also extends to hardware through sc:Hardware and sc:HardwareVersions, allowing for comprehensive tracking of both digital and physical components. Vulnerabilities are represented through sc:Vulnerability and sc:VulnerabilityType, with links to the entities that discover them, providing a detailed view of security risks across software and hardware versions.Cross-reference for Secure Chain Ontology classes, object properties and data properties back to ToC
This section provides details for each class and property defined by Secure Chain Ontology.Classes
- Hardware
- Hardware Version
- License
- Organization
- Person
- Product
- Software
- Software Application
- Software Version
- Vulnerability
- Vulnerability Type
Hardwarec back to ToC or Class ToC
IRI: https://w3id.org/secure-chain/Hardware
- has super-classes
- Product c
- has sub-classes
- Hardware Version c
- is in domain of
- has Hardware Version op
Hardware Versionc back to ToC or Class ToC
IRI: https://w3id.org/secure-chain/HardwareVersion
- has super-classes
- Hardware c
- is in domain of
- version Name dp
- is in range of
- has Hardware Version op, operates On op
Licensec back to ToC or Class ToC
IRI: https://w3id.org/secure-chain/License
- has super-classes
- Creative Work c
Organizationc back to ToC or Class ToC
IRI: http://schema.org/Organization
- Is defined by
- http://schema.org/
- is in domain of
- discover op
Personc back to ToC or Class ToC
IRI: http://schema.org/Person
- Is defined by
- http://schema.org/
- is in domain of
- discover op
Productc back to ToC or Class ToC
IRI: http://schema.org/Product
- Is defined by
- http://schema.org/
- has sub-classes
- Hardware c
Softwarec back to ToC or Class ToC
IRI: https://w3id.org/secure-chain/Software
- has super-classes
- Software Application c
- has sub-classes
- Software Version c
- is in domain of
- has Software Version op
Software Applicationc back to ToC or Class ToC
IRI: http://schema.org/SoftwareApplication
- Is defined by
- http://schema.org/
- has sub-classes
- Software c
Software Versionc back to ToC or Class ToC
IRI: https://w3id.org/secure-chain/SoftwareVersion
- has super-classes
- Software c
- is in domain of
- depends On op, operates On op, version Name dp, vulnerable To op
- is in range of
- depends On op, has Software Version op
Vulnerabilityc back to ToC or Class ToC
IRI: https://w3id.org/secure-chain/Vulnerability
- has super-classes
- Intangible c
- is in domain of
- vulnerability Type op
- is in range of
- discover op, vulnerable To op
Vulnerability Typec back to ToC or Class ToC
IRI: https://w3id.org/secure-chain/VulnerabilityType
- has super-classes
- Intangible c
- is in range of
- vulnerability Type op
Object Properties
- affiliation
- contributor
- depends On
- discover
- has Hardware Version
- has Software Version
- license
- manufacturer
- operates On
- producer
- vulnerability Type
- vulnerable To
affiliationop back to ToC or Object Property ToC
IRI: http://schema.org/affiliation
- Is defined by
- http://schema.org/
contributorop back to ToC or Object Property ToC
IRI: http://schema.org/contributor
- Is defined by
- http://schema.org/
depends Onop back to ToC or Object Property ToC
IRI: https://w3id.org/secure-chain/dependsOn
- has domain
- Software Version c
- has range
- Software Version c
discoverop back to ToC or Object Property ToC
IRI: https://w3id.org/secure-chain/discover
- has domain
- Organization c or Person c
- has range
- Vulnerability c
has Hardware Versionop back to ToC or Object Property ToC
IRI: https://w3id.org/secure-chain/hasHardwareVersion
- has domain
- Hardware c
- has range
- Hardware Version c
has Software Versionop back to ToC or Object Property ToC
IRI: https://w3id.org/secure-chain/hasSoftwareVersion
- has domain
- Software c
- has range
- Software Version c
licenseop back to ToC or Object Property ToC
IRI: http://schema.org/license
- Is defined by
- http://schema.org/
manufacturerop back to ToC or Object Property ToC
IRI: http://schema.org/manufacturer
- Is defined by
- http://schema.org/
operates Onop back to ToC or Object Property ToC
IRI: https://w3id.org/secure-chain/operatesOn
- has domain
- Software Version c
- has range
- Hardware Version c
producerop back to ToC or Object Property ToC
IRI: http://schema.org/producer
- Is defined by
- http://schema.org/
vulnerability Typeop back to ToC or Object Property ToC
IRI: https://w3id.org/secure-chain/vulnerabilityType
- has domain
- Vulnerability c
- has range
- Vulnerability Type c
vulnerable Toop back to ToC or Object Property ToC
IRI: https://w3id.org/secure-chain/vulnerableTo
- has domain
- Software Version c
- has range
- Vulnerability c
Data Properties
- code Repository
- description
- family Name
- given Name
- identifier
- name
- programming Language
- url
- version Name
code Repositorydp back to ToC or Data Property ToC
IRI: http://schema.org/codeRepository
- Is defined by
- http://schema.org/
descriptiondp back to ToC or Data Property ToC
IRI: http://schema.org/description
- Is defined by
- http://schema.org/
emaildp back to ToC or Data Property ToC
IRI: http://schema.org/email
- Is defined by
- http://schema.org/
family Namedp back to ToC or Data Property ToC
IRI: http://schema.org/familyName
- Is defined by
- http://schema.org/
given Namedp back to ToC or Data Property ToC
IRI: http://schema.org/givenName
- Is defined by
- http://schema.org/
identifierdp back to ToC or Data Property ToC
IRI: http://schema.org/identifier
- Is defined by
- http://schema.org/
namedp back to ToC or Data Property ToC
IRI: http://schema.org/name
- Is defined by
- http://schema.org/
programming Languagedp back to ToC or Data Property ToC
IRI: http://schema.org/programmingLanguage
- Is defined by
- http://schema.org/
version Namedp back to ToC or Data Property ToC
IRI: https://w3id.org/secure-chain/versionName
- has domain
- Hardware Version c or Software Version c
- has range
- string
Legend back to ToC
op: Object Properties
dp: Data Properties
Acknowledgments back to ToC
The authors would like to thank Silvio Peroni for developing LODE, a Live OWL Documentation Environment, which is used for representing the Cross Referencing Section of this document and Daniel Garijo for developing Widoco, the program used to create the template used in this documentation.